Page 20 - Service Delivery Review_Volume 14_Number 3_2022
P. 20
ICT Security
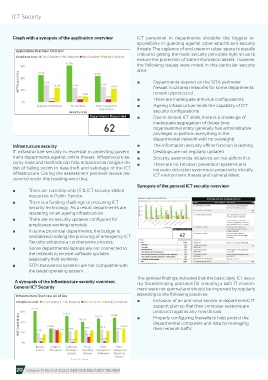
Graph with a synopsis of the application overview ICT personnel in departments shoulder the biggest re-
sponsibility in guarding against cyber-attacks and security
threats. The vigilance of end-users in cyber-space is equally
critical to getting the basic security principles right so as to
ensure the protection of state information assets. However,
the following issues were noted in this particular security
area:
■ Departments depend on the SITA perimeter
firewall: local area networks for some departments
remain unprotected
■ There are inadequate antivirus configurations
■ Ageing infrastructure limits the capability of ICT
security configurations
■ Due to limited ICT skills, there is a challenge of
inadequate segregation of duties (one
organisational entity generally has administrative
privileges to perform everything in the
departmental network with no oversight)
Infrastructure security ■ The information security officer function is lacking
IT infrastructure security is essential in protecting govern- ■ Desktops are not regularly updated
ment departments against online threats. Infrastructure se- ■ Security awareness initiatives are not adhered to
curity tools and methods can help departments mitigate the ■ There are no intrusion prevention systems and
risk of falling victim to data theft and sabotage of the ICT intrusion detection systems to proactively identify
infrastructure. During the assessment pertinent issues dis- ICT environment threats and vulnerabilities.
covered under this heading were that:
Synopsis of the general ICT security overview:
■ There are currently only 1,5 % ICT security skilled
resources in Public Service
■ There is a funding challenge to procuring ICT
security technology. As a result, departments are
operating on an ageing infrastructure
■ There are no security updates configured for
employees working remotely
■ In some provincial departments, the budget is
centralised, making the procuring of emergency ICT
Security solutions a cumbersome process.
■ Some departmental laptops are not connected to
the network to receive software updates
(especially field workers)
■ SITA transversal systems are not compatible with
the latest operating system.
The general findings indicated that the basic daily ICT secu-
A synopsis of the infrastructure security overview: rity housekeeping practises for ensuring a safe IT environ-
General ICT Security ment were not optimal and should be improved by regularly
attending to the following practices:
■ Inclusion of an anti-virus service in departments’ IT
support plan so that their computer systems are
protected against any new threats.
■ Properly configuring firewalls to help protect the
departmental computers and data by managing
their network traffic.
20 Volume 14 No.3 of 2022 | SERVICE DELIVERY REVIEW